Leveraging Your CMTS for Upstream Spectrum Analysis
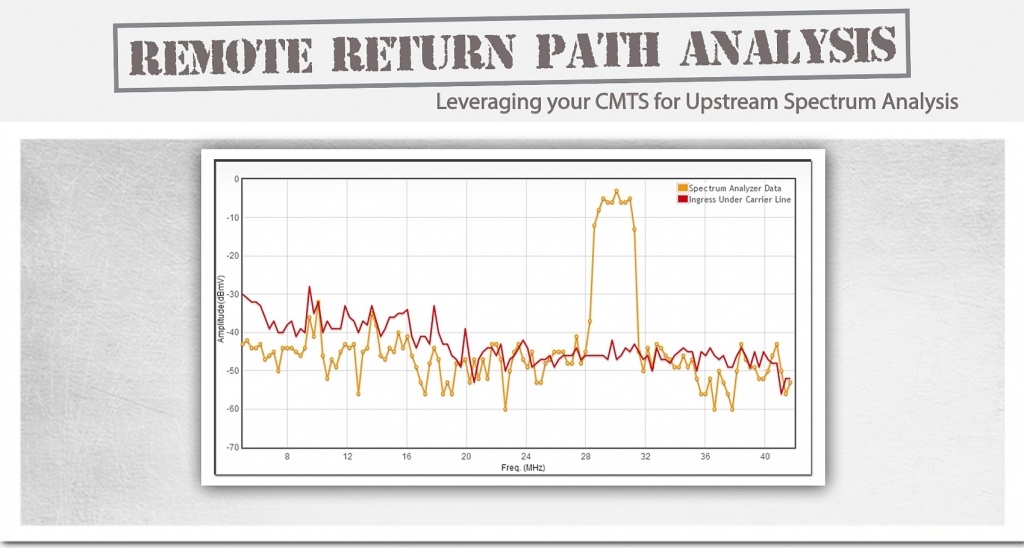
The major problems that operators are having with the upstream path have to do primarily with ingress and noise. Aggravating the troubleshooting process is that often the interfering ingress problems are intermittent. Just as a tech gets close to the problem, it goes away, and he has to wait for it to show up again, perhaps today, maybe tomorrow.
Rick Yuzzi and ZCorum technology officers examine the advantages cable operators can see by identifying and analyzing noise in the return path as part of their overall strategy for network management.
The webinar for the National Cable Television Cooperative (NCTC) on the subject of Remote Return Path Analysis - Leveraging Your CMTS for Upstream Spectrum Analysis focused on managing ingress and noise by monitoring the upstream spectrum path in DOCSIS networks. Specific topics include where noise can enter the plant, sources of noise and their effect on services. In addition, different tools to identify ingress in the plant were discussed.
So exactly how does noise affect the subscriber? As explained in the webinar, “There is a cumulative effect as noise enters the return path, and as noise levels grow there is a point where the CMTS has a hard time hearing the DOCSIS signal. Subscribers may not notice any issue until the level of noise reaches a point where it completely destroys communications or drastically slows down network performance. This will cause a visible degrading of video service, voice quality and slow Internet, and is why monitoring of noise in the spectrum and under the DOCSIS carrier is so crucial.”
The Webinar has been completed, but you still have the chance to view the recording.
About the Author: Marsha Hemmerich
Never miss a post.
Enter your email to subscribe:
- Ask an Expert (12)
- Blog (12)
- Technology (11)
- Hot Topics (8)
- ask a broadband expert (8)
- DOCSIS (7)
- PNM (7)
- proactive network maintenance (7)
- Industry Perspectives (5)
- BEAD (4)
- Broadband Funding (4)
- Customer Service (4)
- FCC (4)
- IIJA (4)
- PreEqualization Analyzer (4)
- correlation groups (4)
- fiber broadband (4)
- fiber optics (4)
- fiber troubleshooting (4)
- interview (4)
- CGNAT (3)
- Carrier Grade NAT (3)
- DDoS Attacks (3)
- DOCSIS pre-equalization (3)
- Diagnostics (3)
- Distributed Denial of Service Attacks (3)
- GPoN (3)
- IPv4 Conservation (3)
- Purchase IPv4 Addresses (3)
- What is DOCSIS PNM (3)
- broadband infrastructure funding (3)
- fiber (3)
- 5G (2)
- CALEA (2)
- CALEA Compliance (2)
- Codeword Errors (2)
- DOCSIS 3.1 (2)
- Distributed Access Architecture (2)
- Group Delay (2)
- ICFR (2)
- IP traffic (2)
- IPv6 migration (2)
- In Channel Frequency Response (2)
- Main Tap Compression (2)
- Marketing (2)
- Micro Reflections (2)
- Millimeter Wave (2)
- OTT (2)
- Rural Broadband (2)
- Types of DDoS Attacks (2)
- Voice Service (2)
- XGS-PON (2)
- broadband data collection (2)
- customer service (2)
- internet issues (2)
- mid-band spectrum (2)
- mmWave (2)
- network traffic (2)
- network virtualization (2)
- state broadband (2)
- state broadband program (2)
- weather-related Internet issues (2)
- 10G (1)
- BDC (1)
- BDC Availability Data Specification (1)
- BDC User Guide (1)
- BEAD Funding (1)
- Broadband Providers (1)
- Broadband Serviceable Location Fabric (1)
- Broadband Serviceable Locations (1)
- C-Band (1)
- CA Certificate Expiration (1)
- CAF II Requirements (1)
- CAF II Testing (1)
- CALEA SSI Plan (1)
- CBRS (1)
- Carpet Bombing (1)
- Citizens Broadband Radio (1)
- Communications Assistance for Law Enforcement Act (1)
- Connect America Fund (1)
- DAA (1)
- DOCSIS 4.0 (1)
- DOCSIS CA Certificate Expiration (1)
- DPoE (1)
- DPoG (1)
- EPoN (1)
- Excel Text Matching (1)
- Extended Spectrum DOCSIS (1)
- Extending HFC Life (1)
- FCC Broadband Map (1)
- FCC data (1)
- FTTH (1)
- FTTx (1)
- Fidelity Communications (1)
- Full Duplex (1)
- Greenfield Broadband (1)
- Hosted VoIP (1)
- IPTV (1)
- IPv4 (1)
- IPv6 (1)
- IPv6 Transition Plan (1)
- LTE (1)
- Low Latency DOCSIS (1)
- MAC/PHY (1)
- Mobile (1)
- Monitoring (1)
- Motivation for DDoS Attacks (1)
- Multi-Vector DDoS Attacks (1)
- NG-PON2 (1)
- NIST (1)
- NIST Cybersecurity Framework (1)
- NIST requirements (1)
- NetFlow (1)
- Network Traffic Management, (1)
- OTT video streaming (1)
- Private Access License (PAL) (1)
- RDOF Auction (1)
- RDOF Voice Requirements (1)
- Remote MAC/PHY (1)
- Remote PHY (1)
- Robocalls (1)
- Rural Broadband Network Advancement Act (1)
- Rural Digital Opportunity Fund (1)
- SSI (1)
- STIR/SHAKEN (1)
- Small Cells (1)
- Streaming (1)
- System Security and Integrity Plan (1)
- TV Viewership Analytics (1)
- TWDM-PON (1)
- TruVizion (1)
- Underserved Locations (1)
- Unserved Locations (1)
- Upstream Analyzer (1)
- Videos (1)
- VoIP (1)
- VoIP revenue (1)
- Wired Broadband (1)
- broadband data collection program (1)
- broadband deployment (1)
- broadband support (1)
- cableLabs (1)
- caf ii (1)
- case study (1)
- cloud-based VoIP (1)
- commercial VoIP (1)
- commercial VoIP revenue (1)
- cpe spectrum capture (1)
- customer service tip (1)
- cyber attacks (1)
- cybersecurity (1)
- dhcp (1)
- downstream spectrum issues (1)
- dual stack implementation (1)
- dynamic spectrum sharing (1)
- electric membership cooperatives (1)
- fiber Internet (1)
- fiber deployment (1)
- forward path monitoring (1)
- free download (1)
- full band capture (1)
- holiday customer service (1)
- holiday tech support (1)
- ingress (1)
- middle mile grant program (1)
- net neutrality (1)
- open access fiber (1)
- open access fiber network (1)
- open access networks (1)
- pppoa (1)
- pppoe (1)
- pre-equalization (1)
- reduced maintenance costs (1)
- remote spectrum analyzer (1)
- return path (1)
- scott helms (1)
- technical paper (1)
- technical support (1)
- vTDR (1)
.
About the Blog
Bloggers
Comments Policy
Guest Blogging
Privacy Policy

Leave a comment: